April 22, 2020
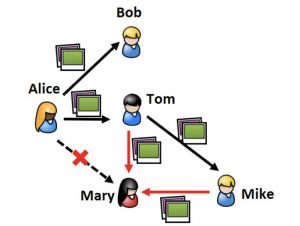
This diagram, provided by Associate Professor Dan Lin, shows how images can easily be shared with an unintended recipient. In this case, Alice unsuccessfully attempted to block Mary from seeing her photos.
More people are turning to social media for human interaction during stay-at-home orders, but one Mizzou Engineering researcher warns that oversharing gives scammers opportunities to steal your private information.
“Because we cannot go out to socialize, people want to share things online for their social needs,” said Dan Lin, an associate professor in Electrical Engineering and Computer Science and director of the I-Privacy Lab. “But it can be risky.”
Before playing along with the latest Facebook challenge or posting that Instagram-worthy picture of your family home, Lin says to consider the following.
Privacy matters
While privacy settings on social media channels have improved over the past several years, it is still easy to bypass that security, Lin warns. Even if you have blocked someone from seeing your information, another user you are connected with can save your information and pass it along to people outside of your connections—sometimes unknowingly.
Bottom line, if you do not want something to be public to everyone, including strangers, it is best not to share it at all, she says.
Beware of games
They seem innocent enough. Facebook users challenge one another to answer a few questions about themselves. But often these games extract sensitive information such as your first job, your first car or your mother’s maiden name—all of which can give hackers answers to commonly used security questions.
Challenges asking you to post an image can pose similar problems. The Better Business Bureau recently warned against posting a senior photo with the name of your high school and graduation year—a challenge marketed as a way to support the Class of 2020.
In more recent days, Facebook users are being asked to share photos of their moms for Mother’s Day. But those images could put moms at risk by revealing identifiable information and can even provide clues as to whether they live alone.
“If you want to celebrate Mom, talking to her is better than sharing her picture with strangers,” Lin said. “I think Mom will feel better.”
Consider your surroundings
Images taken with digital cameras contain metadata that provides information about the file. While many social media platforms automatically remove that information when a photo gets posted, Lin warns that publishing images online without scrubbing metadata can provide hackers with information you did not intend to share. You can remove metadata by opening the properties and details of a file and deleting the values, or by using existing metadata removal software.
Also be aware of what’s in the background of your photo, Lin said. Don’t post images that show your house number, vehicle or unique decorative household items that can help others locate you. These can all reveal personal information about you that you may not want in the public realm.

Dan Lin
Future protection
Lin is currently researching how artificial intelligence can help social media providers offer more advanced levels of privacy.
One method involves predicting what type of photo you’re posting and alerting you as to how that image may be used by others. For instance, if you want to share an image with a selected group of friends, the system would warn you that your photo could still be viewed by friends of those friends, including people you intentionally excluded from the group.
Another strategy would allow social media channels to automatically recommend privacy protections for a particular image based on the type of photo and past user behavior. A family photo, for instance, could come with automatic privacy settings blocking others from sharing or downloading it. A funny picture of your pet, however, might come with fewer security recommendations.
A more advanced method Lin is looking into involves facial replacement in group photos. Rather than blurring out someone’s face in a photo of a class or public setting—which draws the attention of an attacker—she’s devising a way that social media providers could replace a person’s likeness with a synthetic facial image. The change would be subtle enough that those looking at the photo would not be able to tell it had been altered while still allowing someone’s identity to stay private on social media.
Ultimately, Lin said, it’s up to social media companies to determine whether to implement new security strategies. Until then, she said, users should be cautious about what they choose to post. Anything posted online almost never fully disappears, even if you delete it immediately, so nothing is truly private on social media.